New NGate Android malware uses NFC chip to steal credit card data
Hello Questors😊

A new Android malware named NGate can steal money from payment cards by relaying to an attacker's device the data read by the near-field communication (NFC) chip.
Specifically, NGate enables attackers to emulate victims' cards and make unauthorized payments or withdrawal cash from ATMs..
The campaign has been active since November 2023 and is linked to a recent report from ESET on the increased use of progressive web apps (PWAs) and advanced WebAPKs to steal banking credentials from users in the Czechia.
What is NGate?
NGate, besides abusing the functionality of NFCGate to capture NFC traffic and pass it along to another device, prompts users to enter sensitive financial information, including banking client ID, date of birth, and the PIN code for their banking card.
Stealing card data via NFC chip
The attacks start with malicious texts, automated calls with pre-recorded messages, or malvertising to trick victims into installing a malicious PWA, and later WebAPKs, on their devices.
These web apps are promoted as urgent security updates and use the official icon and login interface of the targeted bank to steal client access credentials.
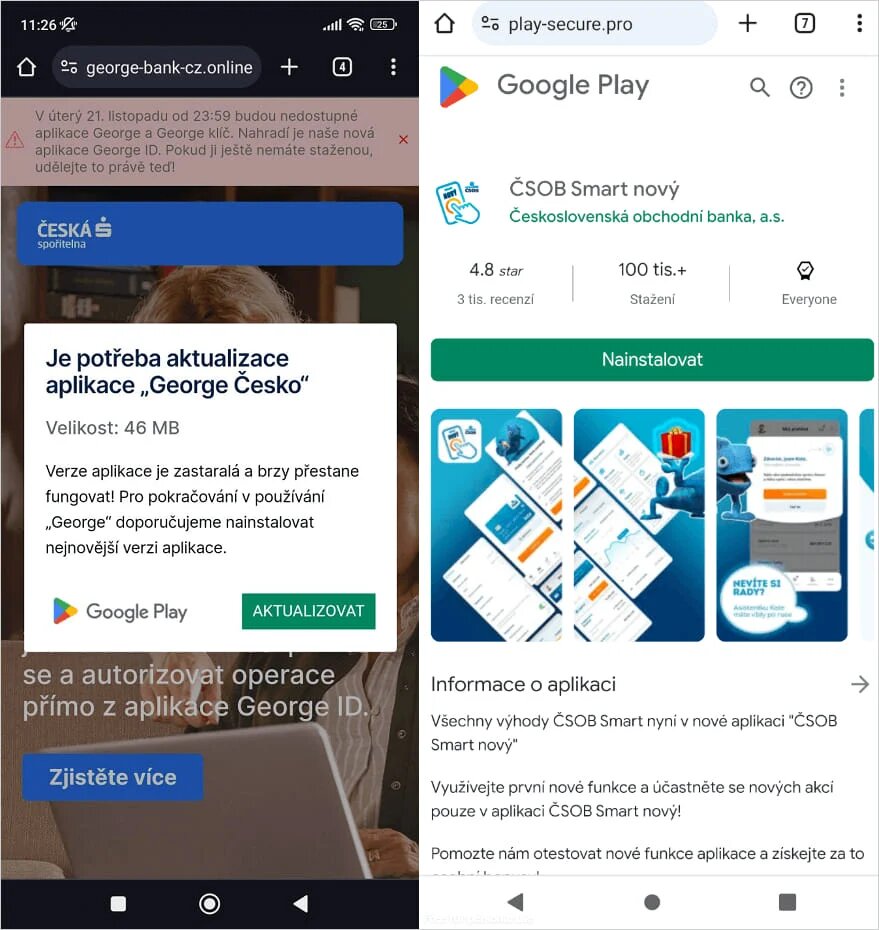
Note: Fake Play Store pages from where the WebAPK is installed and you can also identify playstore pages its orginal or fake.. you can check URL's.
These apps do not require any permission when installed. Instead they abuse the API of the web browser they run in to get the necessary access to the devices hardware components.
This Attack it is called Phishing attack via WebApk.
I really requested to all IQOO family Questors Please do not installed unauthaurize application.
Attacker Doing Phishing attack via webApk to hack victim device.
Once the phishing step is done via the WebAPK, the victim is tricked into also installing NGate via a subsequent step in the second attack phase.
Upon installation, the malware activates an open-source component called 'NFCGate' that was developed by university researchers for NFC testing and experimentation.
The tool supports on-device capturing, relaying, replaying, and cloning features, and does not always require the device to be "rooted" in order to work.
NGate uses the tool to capture NFC data from payment cards in close proximity to the infected device and then relay it to the attacker's device, either directly or through a server.
The attacker may save this data as a virtual card on their device and replay the signal on ATMs that use NFC to withdraw cash, or make a payment at a point-of-sale (PoS) system.
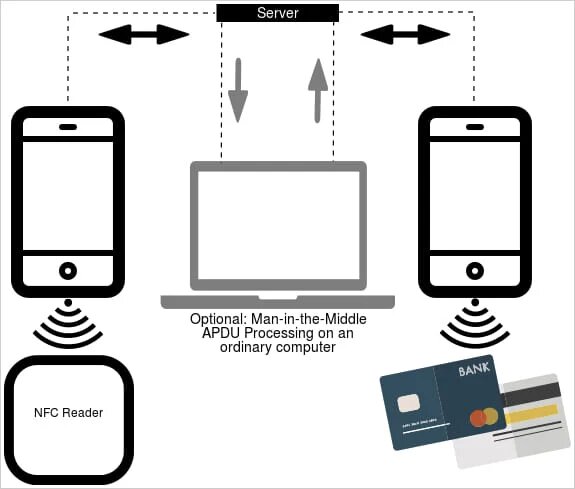
Note: NFC data relay process.
The NFCGate component in NGate can be used to scan and capture card data in wallets and backpacks. In this scenario an attacker at a store could receive the data through a server and make a contactless payment using the victim's card.
What is Social Engineering?
Social engineering is the tactic of manipulating, influencing, or deceiving a victim in order to gain control over a computer system, or to steal personal and financial information. It uses psychological manipulation to trick users into making security mistakes or giving away sensitive information.
Acquiring the card PIN
A cash withdrawal at most ATMs requires the card's PIN code, which the researchers say that it is obtained by social engineering the victim.
After the PWA/WebAPK phishing step is done, the scammers call the victim, pretending they are a bank employee, informing them of a security incident that impacts them.
They then send an SMS with a link to download NGate, supposedly an app to be used for verifying their existing payment card and PIN.
Once the victim scans the card with their device and enters the PIN to "verify" it on the malware's phishing interface, the sensitive information is relayed to the attacker, enabling the withdrawals.
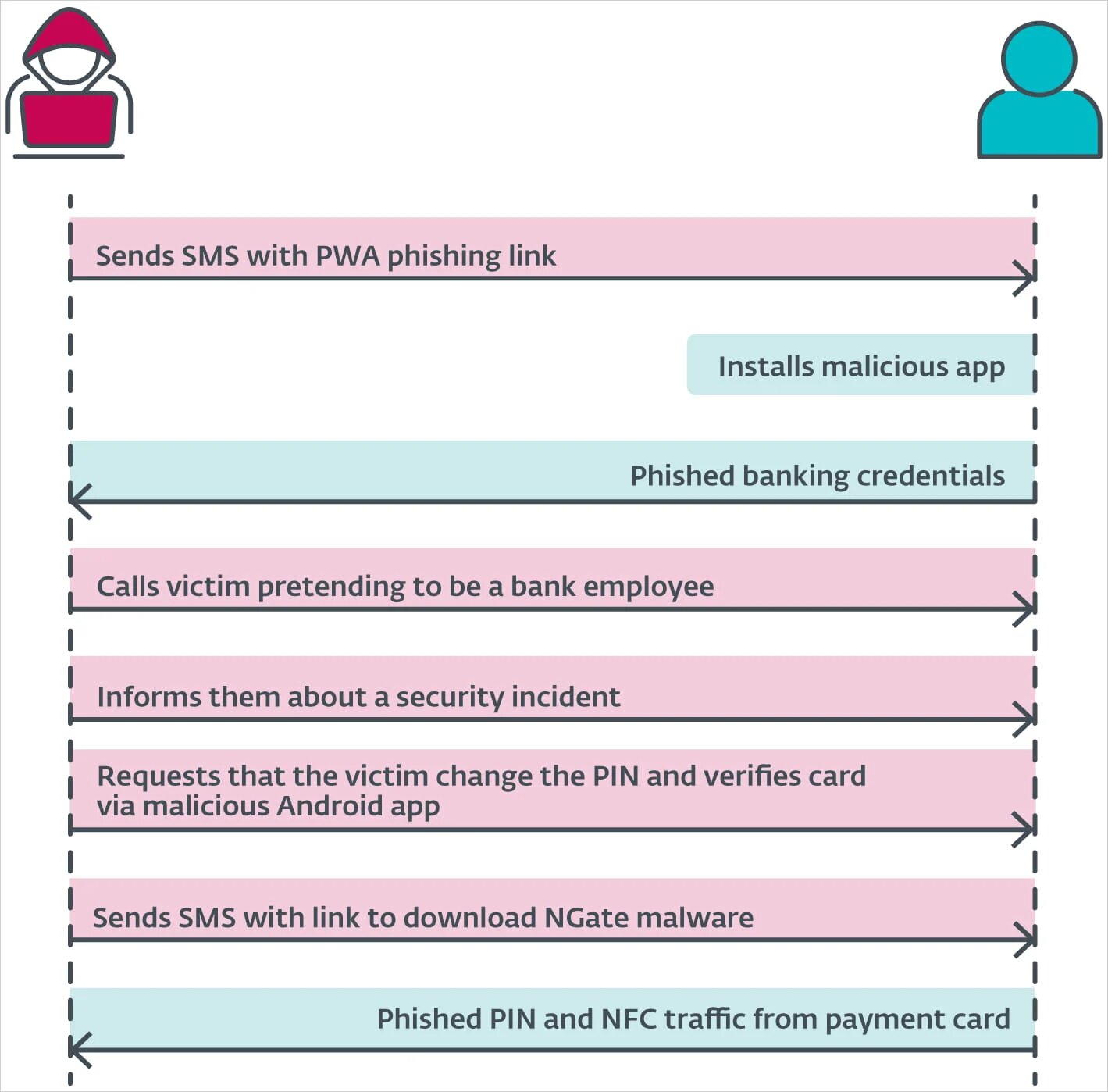
Note: The complete attack overview.
The Czech police already caught one of the cybercriminals performing these withdrawals in Prague, but as the tactic may gain traction, it poses a significant risk for Android users.
ESET also highlights the possibility of cloning area access tags, transport tickets, ID badges, membership cards, and other NFC-powered technologies, so direct money loss isn't the only bad scenario.
NFC (Near-field communication)
If you are not actively using NFC, you can mitigate the risk by disabling your device's NFC chip. On Android, head to Settings > Connected devices > Connection preferences > NFC and turn the toggle to the off position.
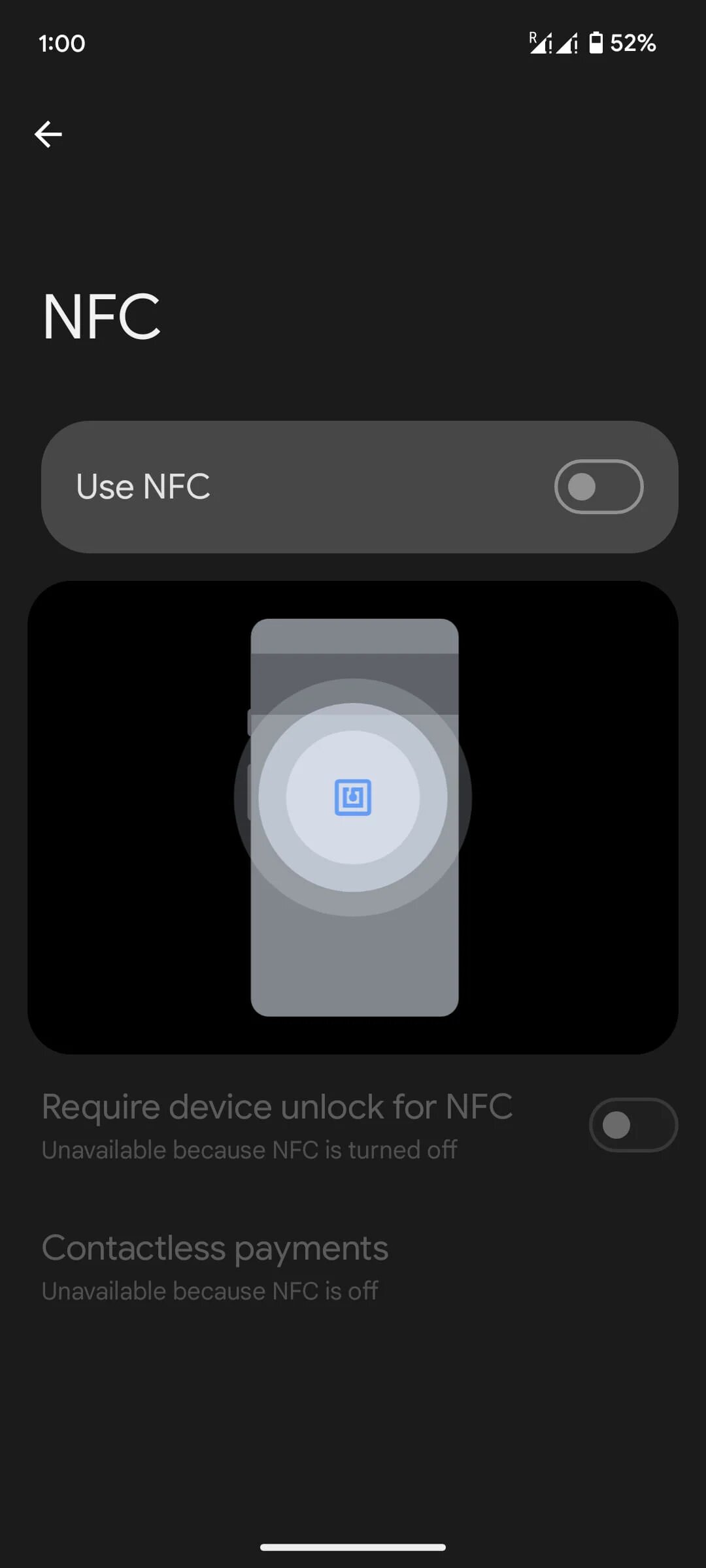
If you need NFC activated at all times, scrutinize all app permissions and restrict access only to those that need it; only install bank apps from the institution's official webpage or Google Play, and ensure the app you're using isn't a WebAPK.
WebAPKs are usually very small in size, are installed straight from a browser page, do not appear under '/data/app' like standard Android apps, and show atypically limited information under Settings > Apps.
I hope this thread helped you....
Thank you.
Signing Off,
#cybersecurity articals
#IQOO CONNECT
Happy Questing
Please sign in
Login and share

























